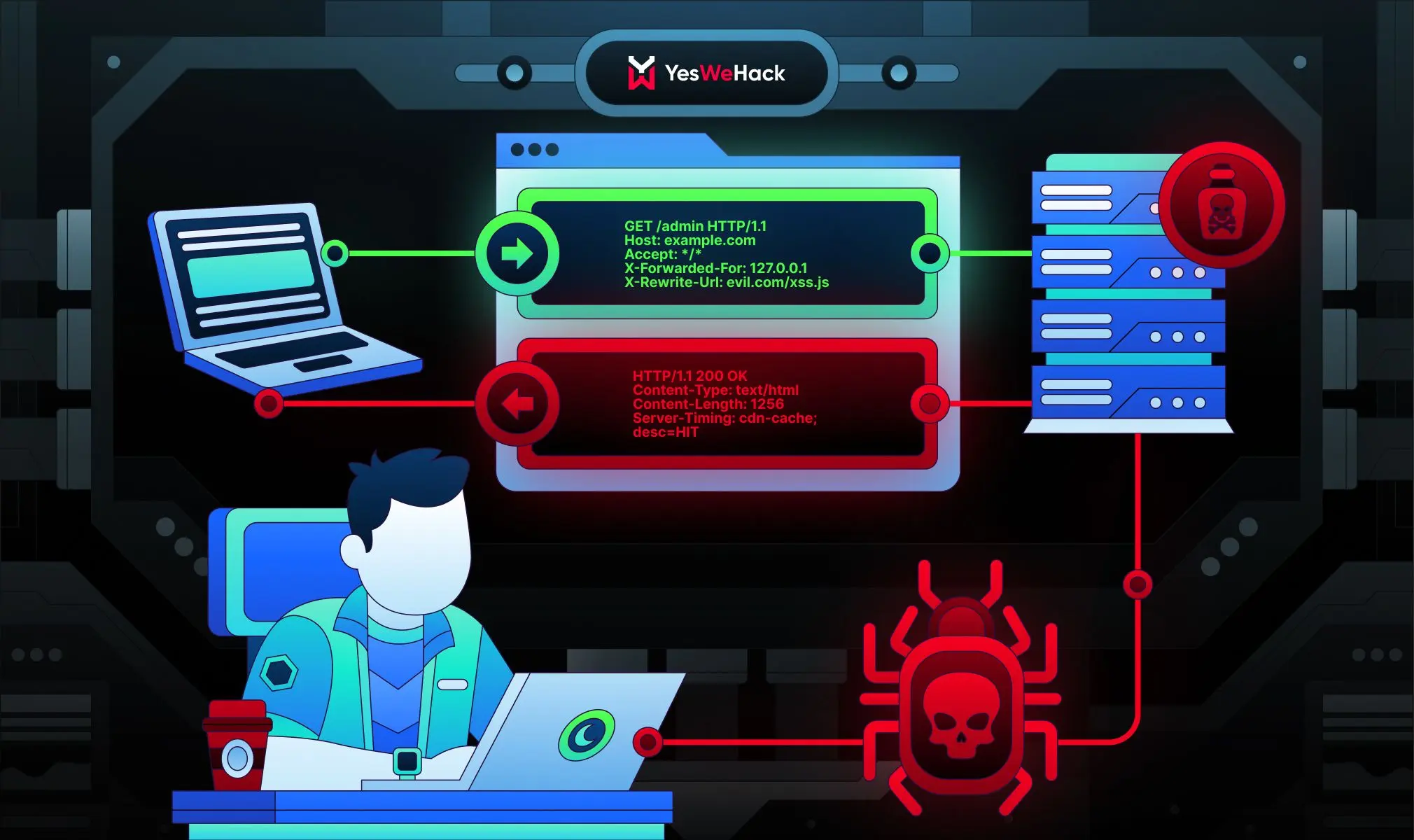
The ultimate Bug Bounty guide to HTTP request smuggling vulnerabilities
Sometimes the web breaks in ways that developers and security teams cannot see. One such failure mode is HTTP request smuggling, which offers security researchers large attack surfaces and high-im...