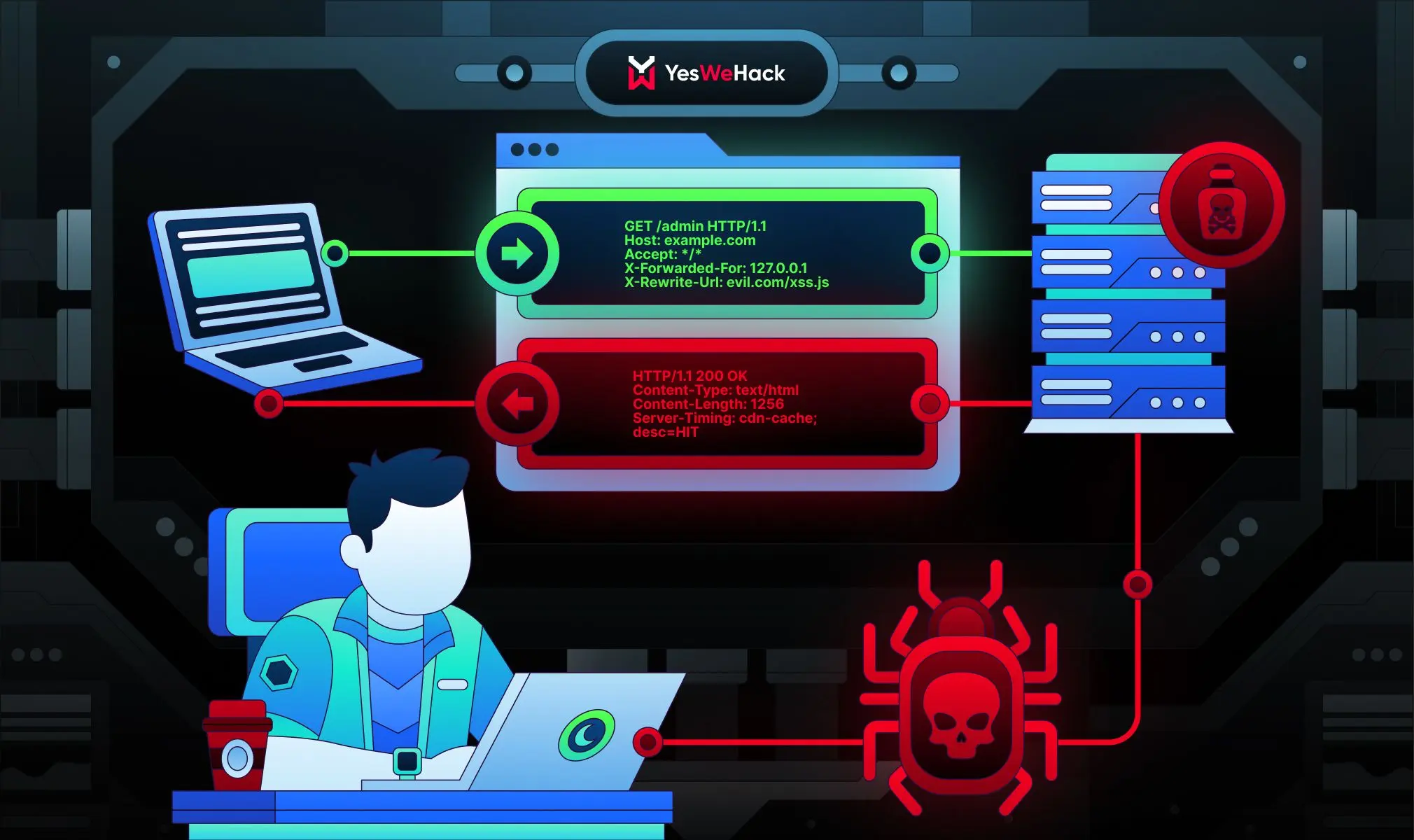
HTTP header hacks: basic and advanced exploit techniques explored
Did you know that manipulating a single HTTP header can unlock high-impact security flaws hidden within a web application?
HTTP headers control how browsers and servers interact with data, so these vulnerabilities can affect the entire application stack.
In this comprehensive guide, we share techniques – both simple and advanced – for exploiting vulnerabilities in HTTP headers, ranging from abusing custom headers to leveraging cache poisoning and reverse proxy misconfigurations.
With real-world examples and easy-to-follow tips, this article will help you spot weaknesses faster and boost your Bug Bounty and ethical hacking skills.
Let’s dive in and uncover how minor modifications to request headers can reveal major security issues!
You can find the full article on YesWeHack’s blog page